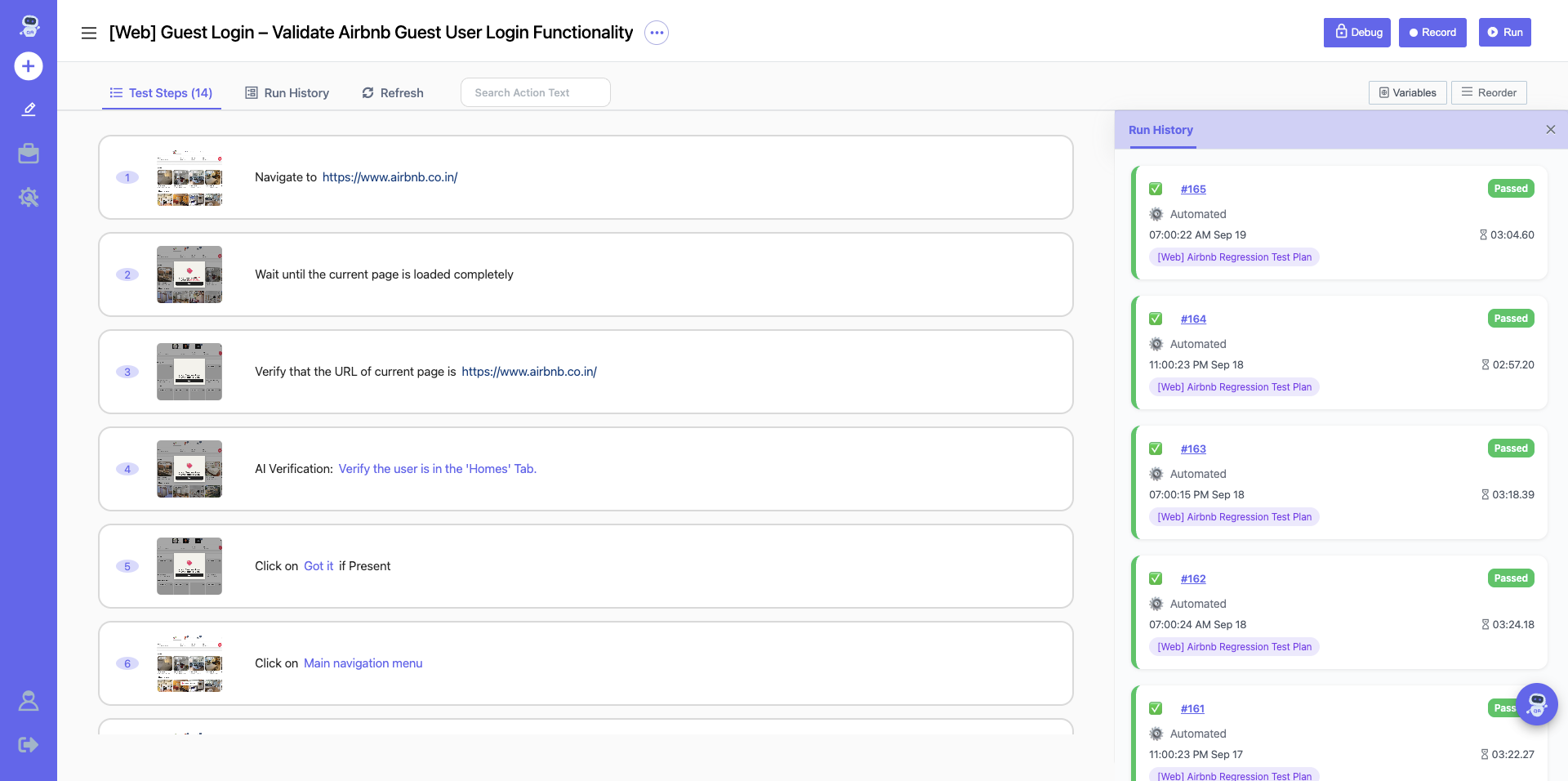
Testing new code just got 10X faster.
The only AI testing platform that understands context

Shrink your testing without wrecking quality
Get faster cycles, cleaner builds, and trustworthy results when you use software testing with our context-aware AI testing platform.
AI Actions per Year
Human Efforts saved
Auto Healing actions
The no-code platform that thinks like an engineer
You don’t need to write scripts or babysit tests. ContextQA keeps them stable as your code changes and catches what breaks before it slows you down.
Catch bugs before users ever see them
AI Testing runs intelligent, automated checks across every build, catching issues the moment they appear. Built on our agentic AI platform, it keeps releases clean and predictable.
Stop wasting hours chasing false failures
With Root-Cause Analysis, ContextQA pinpoints why a test broke. This AI test automation feature helps teams understand what went wrong, so they can fix it and keep momentum moving.
Never fix a flaky test again
Auto-Healing Tests repair themselves as your code evolves, saving teams from repetitive maintenance. Be confident that software testing with AI stays stable.
Never trade speed for stability
Continuous Testing (CI/CD) integrates directly into your workflow, validating code in real time so QA never becomes a bottleneck. Keep releases fast and confidence high with agentic AI test automation.
Smarter decisions with QA data
Analytics & Insights gives full visibility into coverage, stability, and release readiness. Built on our agentic AI platform, it transforms software testing with AI into clear metrics your team can act on.
Describe your tests, and they code themselves
With AI Prompt Engineering, you can turn your ideas into tests. You can refine logic, expand coverage, or target edge cases instantly without code. Stay adaptable with autonomous AI test automation.
How ContextQA makes QA fuel for growth
When QA runs smoothly, everything else gets easier. ContextQA helps testing work quietly in the background so your team can focus on innovation and building what’s next.
Here’s how ContextQA works:
1. AI Agents are always watching
2. Software that gets the nuance
3. Double-check its own work
4. Powering your team’s next move
When testing feels lighter, teams go further
Great products come from teams that work together. ContextQA keeps QA, engineering, and product in sync and compliant with testing that’s easy to understand, simple to share, and maintains itself.
AI handles the
manual upkeep
ContextQA’s autonomous testing agents handle ongoing maintenance automatically, adapting tests as your code evolves so your team can focus on building, not upkeep.
Cover every platform,
every user path
Scale testing,
not your workload
Work with your
current tech stack
See ContextQA in action
Every product, platform, and workflow is unique. ContextQA keeps testing flexible, accurate, and ready for whatever comes next.
SaaS & Enterprise Software
When product updates move fast, QA shouldn’t lag behind. Keep releases reliable with rapid deploys, continuous delivery, and shifting codebases.
Enterprise Applications
Make complex systems testing simple. Keep massive ERP, CRM, and custom enterprise workflows stable with smarter coverage that scales across every environment.
Performance & Accessibility
Always get fast and inclusive AI test automation. Validate performance, accessibility, and UX consistency across every release, so every user experience feels smooth and reliable.
ContextQA raises
the QA bar
Our agentic AI platform replaces brittle scripts with true AI test automation and advanced features.
| Features | Other Platforms |
|
|---|---|---|
| AI Auto Heal and Heatmap | No | Yes |
| Mobile Testing and Show Coverage | Limited | Yes |
| Agentic AI for Dynamic and Proactive Testing | No | Yes |
| Root Cause and Impact Analysis | Limited / Requires Multiple Tools | Yes |
| On Prem / VPC Deployment (AI Privacy) | Limited | Yes |
| No Vendor Lock in (Export Code) | Limited | Yes |
| Unlimited Parallel Execution | Limited | Yes |
| Dynamic Application Security Testing | No | Yes |
| Low Code / No Code Automation | Most Support | Yes |
| Salesforce Testing | Limited | Yes |
Trusted by leading engineering and QA teams


















See why developers love ContextQA

Raul P.
QA Enginee
Vaibhav K.
CEO
Vani B.
Quality Assurance Engineer
Janice G.
Customer Service Specialist
Lisa M.
QA
Thomas Lejars
Co-founder, ZygonWe take testing as seriously as your data
Run ContextQA in your environment with secure on-prem or private cloud options. Your data is protected with SOC 2, ISO 27001, and GDPR compliance.






