Tokens serve as digital keys that authenticate users and grant access to various online services, such as email, social media, and banking platforms. These tokens are stored in browsers to streamline user logins and maintain session persistence across websites.
The convenience of token-based authentication has significantly enhanced user experience, eliminating the need to enter credentials repeatedly. However, with this convenience comes the responsibility of safeguarding these tokens, as they hold the keys to a user’s digital identity.
Understanding Browser Tokens
A. Definition of Browser Tokens
Browser tokens are small pieces of data that serve as digital identifiers or authentication credentials stored within web browsers. These tokens play a crucial role in facilitating secure communication between users and online services. Essentially, they act as digital keys that grant access to specific resources or functionalities on websites.
Tokens are generated during the authentication process, typically after a user successfully logs in to a website or online service. Once generated, these tokens are stored locally in the user’s browser for future use, allowing them to remain logged in and access secured areas without the need to re-enter their credentials each time.
B. Common Types of Tokens
- Authentication Tokens: These tokens verify a user’s identity and are generated during the login process. Authentication tokens, such as JSON Web Tokens (JWT) or OAuth tokens, are used to authenticate users and grant them access to protected resources.
- Session Tokens: Session tokens are created once a user successfully logs in and are used to maintain the user’s session across multiple requests. They help websites recognize and associate actions with a specific user during a browsing session.
- CSRF Tokens: Cross-Site Request Forgery (CSRF) tokens are designed to prevent unauthorized actions on behalf of a user. They are often used in forms and transactions to ensure that the request is legitimate and initiated by the authenticated user.
- Refresh Tokens: Refresh tokens are part of token-based authentication systems and are used to obtain new access tokens without requiring the user to re-enter their credentials. They enhance security by minimizing the exposure of access tokens.
C. Role of Tokens in Web Security
Tokens play a pivotal role in web security by providing a secure and efficient means of authentication and authorization. The key aspects of their role include:
- Authentication: Tokens serve as proof of a user’s identity, allowing them to access secured areas of a website or online service without repeatedly entering their credentials. This enhances user experience while ensuring a secure login process.
- Authorization: By assigning specific permissions to tokens, websites can control the actions a user is allowed to perform. This granular authorization helps prevent unauthorized access to sensitive information or functionalities.
- Session Management: Session tokens contribute to the management of user sessions, allowing websites to recognize and retain user preferences, settings, and activities across multiple interactions. This improves user convenience and engagement.
Understanding the significance of browser tokens is crucial for users to appreciate the security implications and take proactive measures to protect these tokens from unauthorized access or exploitation. In the subsequent sections, we will delve into effective strategies to secure and master the storage of these vital digital keys within browsers.
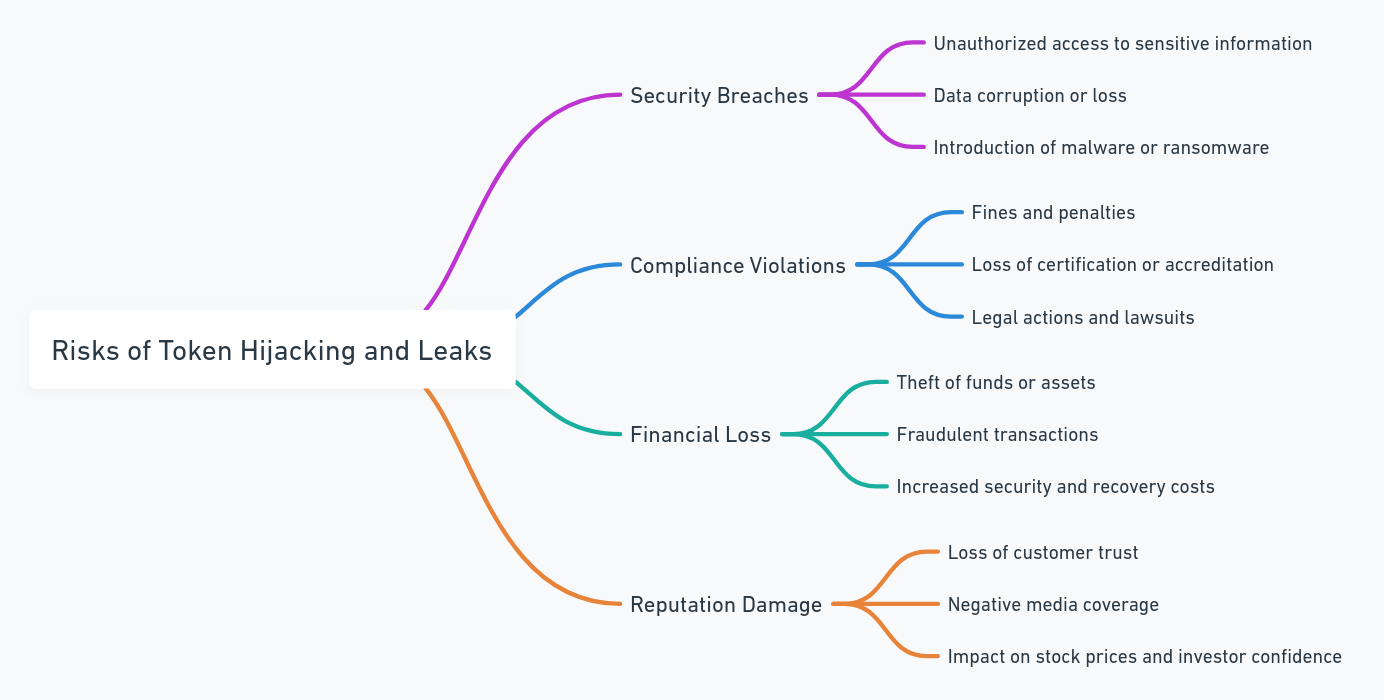
Risks of Token Hijacking and Leaks
A. Overview of Token Hijacking
Token hijacking refers to the unauthorized acquisition of user tokens by malicious entities. Cybercriminals exploit vulnerabilities in the security mechanisms of web applications or browsers to gain access to these tokens. Once hijacked, these tokens can be used to impersonate the legitimate user, leading to a range of malicious activities.
Common methods of token hijacking include cross-site scripting (XSS) attacks, where attackers inject malicious scripts into web pages to steal tokens, and man-in-the-middle (MITM) attacks, where communication between the user and the server is intercepted, allowing attackers to capture tokens.
B. Consequences of Token Leaks
The consequences of token leaks can be severe and have far-reaching implications for both individuals and organizations. Some of the key consequences include:
- Identity Theft: Hijacked tokens can be used to impersonate users, leading to identity theft. Attackers may gain unauthorized access to personal accounts, financial information, and even sensitive business systems.
- Unauthorized Access: With access tokens in hand, attackers can bypass authentication mechanisms and gain unauthorized entry into various online services, compromising the privacy and security of user accounts.
- Financial Loss: Token hijacking can lead to unauthorized transactions, causing financial losses for individuals and organizations. Attackers may exploit stolen tokens to make purchases, transfer funds, or engage in fraudulent activities.
- Data Breaches: Token leaks can result in the exposure of sensitive data stored on web applications. This can include personal information, passwords, and other confidential data, leading to broader data breaches.
C. Real-World Examples of Security Breaches Due to Token Vulnerabilities
- Facebook Access Token Breach (2018): In 2018, Facebook experienced a security breach that affected nearly 50 million user accounts. Attackers exploited a vulnerability in the “View As” feature, allowing them to steal access tokens. This breach compromised user privacy and led to concerns about unauthorized access to personal information.
- Equifax Data Breach (2017): While not specifically related to token hijacking, the Equifax data breach highlights the severe consequences of unauthorized access. Hackers exploited a vulnerability in Equifax’s website, gaining access to sensitive information such as names, Social Security numbers, and credit card details, affecting over 147 million individuals.
- Twitter Bitcoin Scam (2020): In a high-profile incident, attackers gained access to several prominent Twitter accounts, including those of Barack Obama, Elon Musk, and Bill Gates. The attackers used the compromised accounts to promote a Bitcoin scam, urging followers to send cryptocurrency to a specified address. The breach
Browser Token Storage Mechanisms
Explanation of Local Storage:
Local storage is a web storage mechanism available in web browsers that allows websites to store data persistently on a user’s device. This storage is typically implemented using the localStorage API in JavaScript. It enables websites to save key-value pairs directly in the user’s browser, making it a convenient option for storing various types of data, including tokens.
Pros and Cons of Using Local Storage for Tokens
Pros:
- Persistence: Data stored in local storage persists across browser sessions, allowing users to remain logged in even after closing and reopening the browser.
- Ease of Use: Local storage is easy to implement and can be accessed using simple JavaScript commands, making it a developer-friendly option.
- Increased Performance: Retrieving data from local storage is generally faster than making repeated server requests for tokens, contributing to a smoother user experience.
Cons:
- Security Risks: Local storage is vulnerable to cross-site scripting (XSS) attacks, where malicious scripts injected into a website can access and manipulate data stored in local storage.
- No Expiration Mechanism: Tokens stored in local storage do not have built-in expiration mechanisms. This means that even if a user logs out, the token may remain in local storage, posing a security risk.
- Limited to Same-Origin Policy: Local storage is subject to the same-origin policy, which restricts access to data stored by a website to only that specific website. This can limit the use of tokens across multiple domains.
Best Practices for Securing Tokens in Local Storage:
To enhance the security of tokens stored in local storage, it’s essential to follow best practices:
- Use HTTPS: Ensure that your website uses HTTPS to encrypt data transmitted between the browser and server, reducing the risk of man-in-the-middle attacks.
- Implement Same-Site Cookies: Set the SameSite attribute for cookies to restrict cross-site requests, mitigating the risk of cross-site request forgery (CSRF) attacks.
- Token Encryption: Consider encrypting tokens before storing them in local storage. This adds an extra layer of security, making it more challenging for attackers to misuse the stored data in the event of a security breach.
- Regularly Rotate Tokens: Implement token rotation strategies to regularly change and update tokens. This minimizes the impact of potential token leaks or unauthorized access.
- Use Secure Authentication Methods: Implement secure authentication methods, such as multi-factor authentication (MFA), to add an additional layer of protection even if tokens are compromised.
By adhering to these best practices, developers and users alike can minimize the risks associated with storing tokens in local storage, enhancing the overall security of browser token storage mechanisms.
Best Practices for Secure Token Storage
Importance of Encrypting Tokens:
Encrypting tokens is a fundamental practice in securing token storage, as it adds an additional layer of protection against unauthorized access. Encryption transforms the plaintext token into a ciphertext using an algorithm and a secret key. This ensures that even if an attacker gains access to the stored tokens, they cannot decipher the sensitive information without the proper decryption key.
The importance of encrypting tokens includes:
- Confidentiality: Encryption safeguards the confidentiality of tokens, preventing unauthorized parties from understanding the information contained within them.
- Mitigating Insider Threats: In the event of a security breach or insider threat, encrypted tokens make it significantly more challenging for malicious actors to misuse the information they obtain.
- Compliance Requirements: Many data protection regulations and standards require the use of encryption to protect sensitive information, ensuring compliance with legal and regulatory frameworks.
Techniques for Token Obfuscation:
Token obfuscation involves disguising tokens to make them less recognizable and harder to exploit. Obfuscation techniques add an extra layer of security by making it more difficult for attackers to glean information even if they gain access to the stored tokens. Common techniques include:
- Salting: Adding a random and unique value (salt) to each token before encryption helps prevent precomputed attacks. Salting ensures that even if two identical tokens are encrypted, the resulting ciphertexts will be different due to the unique salt.
- Hashing: Applying a one-way hash function to tokens before storage makes it computationally infeasible for attackers to reverse the process and obtain the original token. However, hashing alone may not be sufficient, as it lacks the ability to decrypt the information when needed.
- Randomization: Introducing randomness to the token or its storage location can make it harder for attackers to predict the token’s value or location within the storage mechanism.
Encryption Algorithms and Considerations:
Choosing robust encryption algorithms is crucial for effective token protection. Consider the following factors when selecting encryption algorithms:
- Algorithm Strength: Use widely recognized and accepted encryption algorithms that are considered secure against known cryptographic attacks. Common choices include AES (Advanced Encryption Standard) for symmetric encryption and RSA for asymmetric encryption.
- Key Management: Implement secure key management practices to safeguard encryption keys. Regularly rotate and update keys, and ensure that they are stored in a separate, secure location from the encrypted data.
- Forward Secrecy: Consider using encryption algorithms that support forward secrecy, ensuring that even if one encryption key is compromised, past communications and stored data remain secure.
Case Studies
A. Successful Implementations of Secure Token Storage
- Google’s Implementation of Token Security:
- Overview: Google employs robust security measures to protect user tokens across its various services, including Gmail, Google Drive, and Google Calendar.
- Key Features:
- Encryption: Google uses strong encryption algorithms to protect user tokens stored on its servers, ensuring the confidentiality of user data.
- Token Rotation: Google implements token rotation strategies to regularly change and update user tokens, minimizing the impact of potential security breaches.
- Multi-Factor Authentication (MFA): Google encourages users to enable MFA, adding an additional layer of security to the authentication process.
- Financial Institutions’ Token Security Practices:
- Overview: Many financial institutions prioritize token security due to the sensitive nature of financial transactions and user information.
- Key Features:
- End-to-End Encryption: Financial institutions often implement end-to-end encryption to protect the entire transaction process, from user input to token storage and communication with servers.
- Secure Key Management: Emphasis is placed on secure key management practices to safeguard encryption keys, ensuring that unauthorized access to keys is mitigated.
- Regular Security Audits: Financial institutions conduct regular security audits to identify and address vulnerabilities in token storage systems, enhancing overall security.
B. Examples of Security Breaches Due to Inadequate Token Storage Strategies
- MyFitnessPal Data Breach (2018):
- Overview: MyFitnessPal, a popular fitness and nutrition app, experienced a data breach that affected approximately 150 million user accounts.
- Cause: The breach occurred due to the compromise of usernames, email addresses, and hashed passwords. While not directly related to token storage, the incident highlights the risks of inadequate security measures in protecting user data.
- Dixons Carphone Data Breach (2017):
- Overview: Dixons Carphone, a UK-based electronics retailer, suffered a data breach that impacted 10 million customer records.
- Cause: The breach resulted from a cyberattack that accessed personal data, including names, addresses, and email addresses. While not specifically related to token storage, the incident underscores the importance of securing sensitive user information.
- Yahoo Data Breach (2013-2014):
- Overview: Yahoo experienced one of the largest data breaches in history, affecting all of its 3 billion user accounts.
- Cause: The breach involved the theft of user account information, including encrypted and unencrypted security questions and answers. Although not directly tied to token storage, the incident highlights the broader implications of inadequate security practices.
These case studies illustrate the importance of robust token storage strategies and security measures. Successful implementations emphasize encryption, token rotation, and proactive security measures, while breaches underscore the need.
Prevent Hijacking & Leaks
Browser tokens, serving as digital keys for authentication and authorization, streamline user experiences but also introduce significant security risks if not handled with care. Understanding the risks associated with token hijacking and leaks is crucial for users and developers alike.
As we navigate an increasingly interconnected online environment, developers play a pivotal role in shaping the security landscape. It is crucial for developers to prioritize robust token storage strategies, implementing best practices to fortify browser security.
By adopting secure coding practices, staying informed about emerging threats, and proactively addressing vulnerabilities, developers contribute to a safer online experience for users.
You may also be interested in: Advanced Feature for Software Testing | ContextQA
Book a Demo and experience ContextQA testing tool in action with a complimentary, no-obligation session tailored to your business needs.
We make it easy to get started with ContextQA tool: Start Free Trial.